Phishing is another problem solved by password managers

Software can be vigilant and precise, but you can count on people to be lazy and careless, at least some of the time. Even the most vigilant people are, after all, human.
This is the bug in the human component on which phishing attacks rely. The web page may look exactly like the page you expect and even the domain of the page may look close. The more targeted the attack, which usually translates into a higher-value target, the more you can know about the target and the easier it is to make it convincing.
But the phony login is almost certainly not coming from the same domain as the real login. Telling whether this is the case can be tricky even for an experienced person, let alone a novice. But it's one of the things a password manager does well and with ease.
There are many fine password managers for individual users and for enterprises. I personally use LastPass and I'm very happy with it. Consider the example below, which is the Edit page for the LastPass record for my WordPress site:
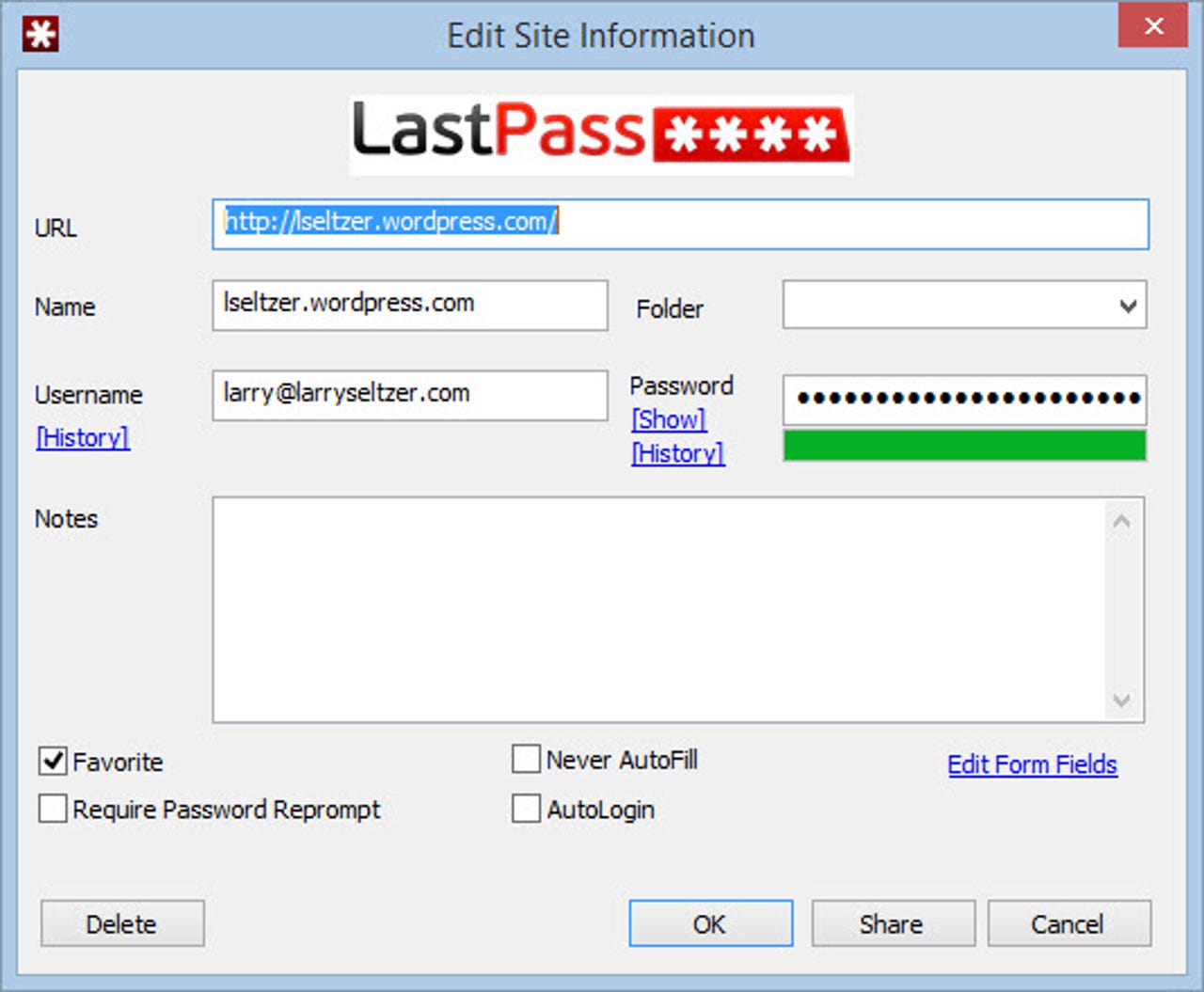
The highlighted field includes the domain for which the credentials in this record are used. LastPass won't present them for use on any other domain. It knows the domain of the login page and cannot be fooled. I'm sure all password managers do the same.
There has been some false information about this feature. A paper "Password Managers: Attacks and Defenses," which was recently presented at Usenix Security 2014, casually makes claims about weaknesses in password managers, including LastPass. For instance:
LastPass: Unlike Chrome and Safari, for triggering autofilling, LastPass only requires that user click a button shown on top of the page. Once this button is clicked all fields in the form (both hidden and visible) gets filled. This makes it very easy for an attacker to create a crafted form showing only fields like name and email address while stealing additional information, such as credit cards, or a Social Security Number, through hidden fields.
Perhaps some password managers are this stupid, but not all of them and certainly not LastPass. When you encounter such a site in LastPass it displays a "LASTPASS SECURITY WARNING" dialog box:
AR + VR
It doesn't stop there. If you follow through on best practices for password managers and make all your passwords strong and unique, you're even less likely to be fooled. I recently went through this exercise with my passwords. Now my passwords are all strings like "uyxK8ZIA4uxD". I am now utterly dependant on LastPass because I don't know any of my passwords by heart. This is a good thing.
LastPass doesn't work 100% of the time. On sites or devices where there's a problem, it's possible to get at your credentials in the LastPass software, but it's necessarily a somewhat cumbersome process. This process forces you to think about where you are and what you're logging into. The most common circumstances where you need to do this is on a mobile device, where the operating systems are unfriendly to password managers.
Like they say, the most insecure part of the system is the one typing on the keyboard. Thus, practical security considerations dictate saving the user from opportunities to compromise himself, and password managers do this well. The way LastPass CEO and Co-Founder Joe Siegrist puts it is "if you don't know your passwords, they can't be phished."