CERT to Microsoft: Don't kill EMET, Windows 10 will be less secure without it

A CERT researcher disputes Microsoft's argument that Windows 10 has "all the mitigation features that EMET administrators have come to rely on".
Microsoft says its EMET security toolkit is redundant because Windows 10 has all its features, but that's not true, says a vulnerability analyst from Carnegie Mellon University's CERT.
For seven years EMET, or Enhanced Mitigation Experience Toolkit, has been the go-to tool for Windows shops that can't patch a new flaw but still want to protect the network.
EMET provides a number of exploit mitigations that can protect otherwise vulnerable systems, even when a bug isn't in a Microsoft product.
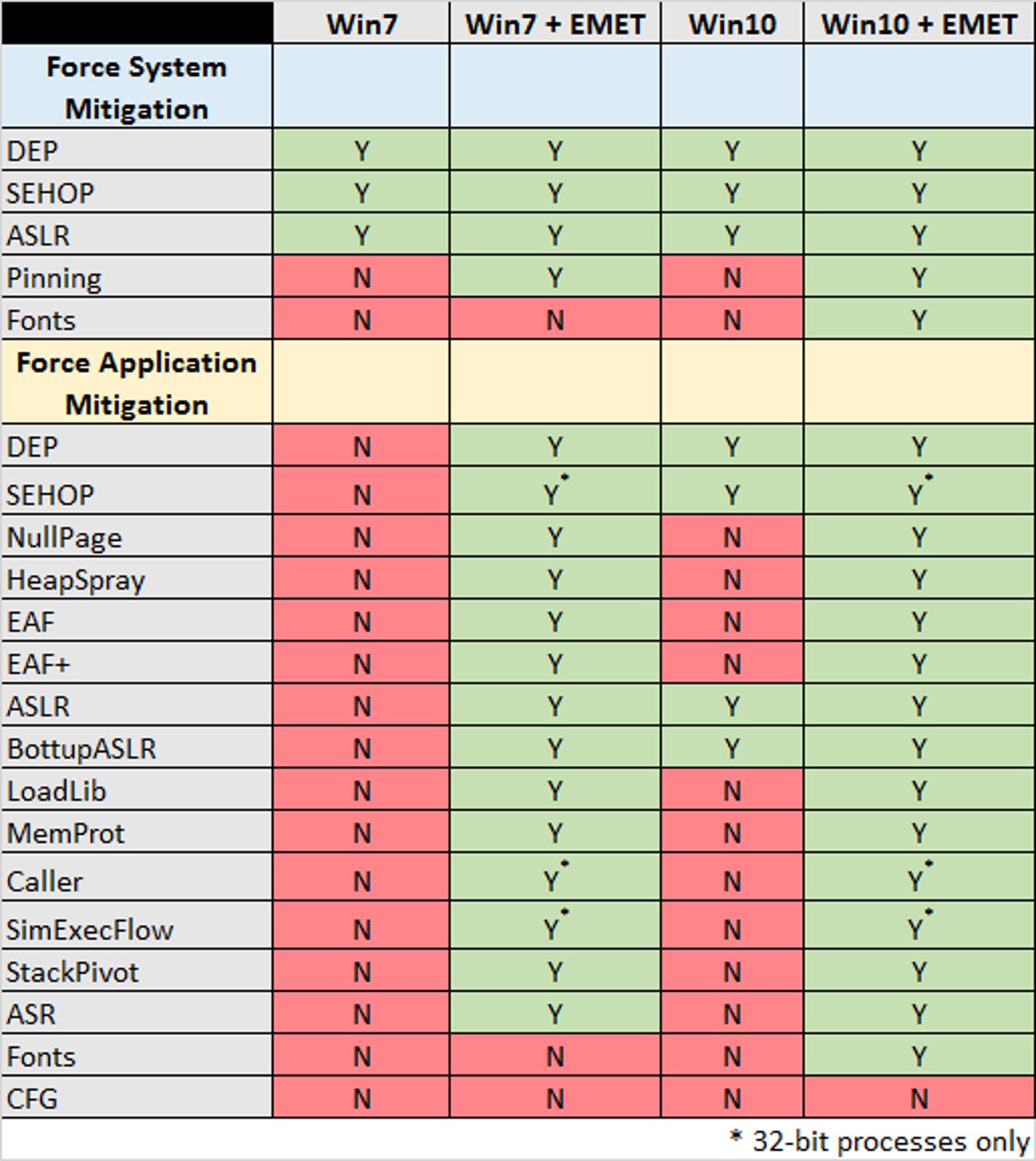
However, earlier this month Microsoft announced plans to abandon EMET since, "Windows 10 includes all of the mitigation features that EMET administrators have come to rely on such as DEP, ASLR, and Control Flow Guard (CFG) along with many new mitigations to prevent bypasses in UAC and exploits targeting the browser".
Jeffrey Sutherland, a principal lead program manager in Microsoft's OS security team, said EMET can't keep up with modern threats and that it's easy to find "trivial bypasses" for it online.
Arguing that customers wanted EMET features built into Windows 10, Microsoft decided it will stop patching EMET after July 31, 2018 and encouraged customers who want better security to switch to Windows 10.
CERT vulnerability analyst Will Dormann this week called on Microsoft to reverse its decision to retire EMET, arguing that Windows 10 does not provide the same protections as EMET. Dorman also shows that Windows 7 with EMET is better protected than Windows 10 without it.
The CERT Division is part of the non-profit, federally-funded Software Engineering Institute research-and-development center operated by Carnegie Mellon University.
Windows 10 does provide some "nice exploit mitigation", says Dormann, but EMET does a better job of protecting non-Microsoft applications that don't always take advantage of underlying Windows exploit mitigations.
"The EMET library can modify the behavior of the target application by providing additional protections," explains Dormann.
"The application-specific-protection capability provided by EMET is where EMET really adds value. Because we cannot rely on all software vendors to produce code that uses all the exploit mitigations available, EMET puts this control back in our hands."
If customers opt against using EMET after Microsoft's end of life for the toolkit, Dormann recommends running an inventory of all software that would still be in use after Microsoft's cut-off date.
The date is even more important for products that don't receive patches from vendors. Dormann notes that Office 2007, which reaches end of support this year, will soon fit that category.
"With such out-of-support applications, it is even more important to provide additional exploit protection with a product like EMET," argues Dormann.