Microsoft: Windows 10 will stop a ransomware epidemic when antivirus fails

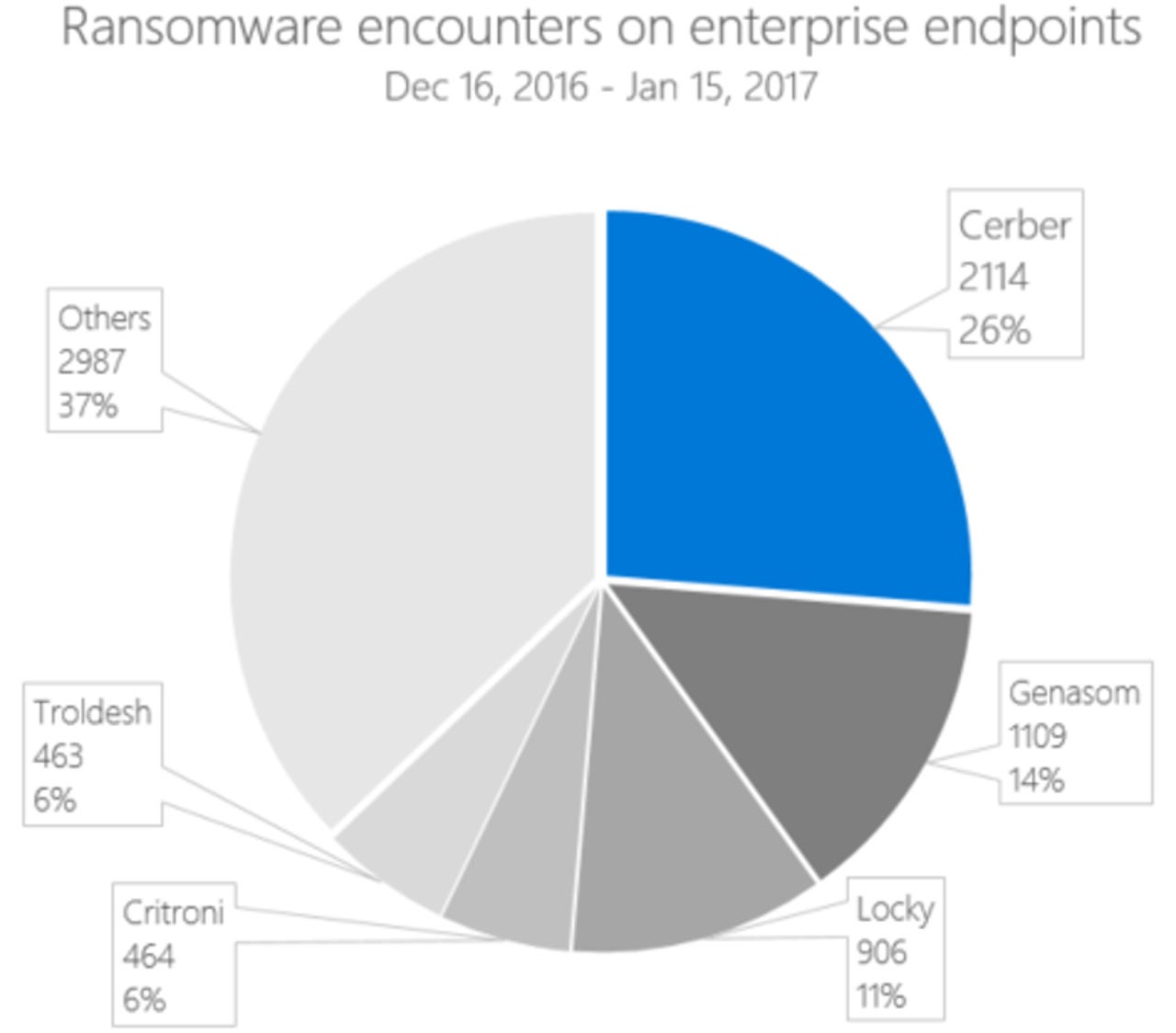
Microsoft's research shows the Cerber family of file-encryptors has been behind many recent ransomware attacks.
When your antivirus fails to block ransomware, Windows 10 still can stop it becoming a major outbreak on the corporate network, according to Microsoft.
It argues that ransomware is one more reason organizations need to move to Windows 10 enterprise, whose built-in Windows Defender Advanced Threat Protection (ATP) can nip ransomware breaches in the bud before they become a nightmare, even if desktop antimalware happens to miss a single instance.
The company has presented new research into the Cerber family of file-encryptors, which dominated ransomware encounters on enterprise end-points between December 16 and January 15, and how Windows Defender ATP countered the threat.
"Our research into prevalent ransomware families reveals that delivery campaigns can typically stretch for days or even weeks, all the while employing similar files and techniques. As long as enterprises can quickly investigate the first cases of infection or 'patient zero', they can often effectively stop ransomware epidemics," says Tommy Blizard, a member of Microsoft's Windows Defender ATP research team.
Since there are common techniques among different families, Blizard contends that what works for Cerber can also help track down other variants of ransomware, enabling a quicker response by security operations.
The company has of late been ramping up its calls for enterprise to migrate to Windows 10, in particular the many organizations still on Windows 7, which Microsoft execs say can no longer meet the "high security requirements of IT departments".
Meanwhile, Windows 10 Defender ATP will get a host of new defenses in the upcoming Creators Update due in April, including new sensors to detect in-memory malware and kernel level exploits, the ability to add new intelligence sources, and better tools to isolate infected machines and conduct forensics.
And as Microsoft highlighted recently, its hardening of the Windows 10 Anniversary Update enabled it to block two previously unseen exploits, even without the patches required by earlier versions.
Microsoft's Blizard highlights that the current version of Defender ATP successfully detected a PowerShell command designed to deliver Cerber to a machine. It also created an alert when the PowerShell script connected to a TOR hidden site to download an executable.
"Security operations center (SOC) personnel could use such alerts to get the source IP and block this IP address at the firewall, preventing other machines from downloading the executable. In this case, the downloaded executable was the ransomware payload," Blizard says.
Security personnel can, for example, use a payload file name to search the Defender ATP console for other instances of the same files on the network. From there, they can look at the source IP address that hosted the payload and block that address at the firewall.
Windows Defender ATP was also able to detect how Cerber automatically launched after the payload was downloaded, and then the actions it takes just before encrypting files, such as efforts to prevent future attempts at using backups to recover.
The alerts are designed to give security pros contextual information and help focus an investigation to prevent an outbreak.
"Their research supports machine-learning models and behavioral-detection algorithms that detect ransomware at different stages of the kill chain, during delivery by email or using exploit kits, up to the point when victims make ransom payments," Blizard notes.