Verizon's data breach report highlights how unsecured cloud storage opens door to attacks

The plague of enterprises leaving cloud storage holding private data unprotected is starting to show up in the security statistics and is one of the few attacks on the rise, according to the Verizon Data Breach Investigation Report for 2020.
That reality is both good and bad, said Gabe Bassett, senior information security data scientist at Verizon Enterprise. The bad news is that misconfiguration errors still exist. The good news is that companies are reporting these breaches more and quantifying the issue. "I don't think it is a case of enterprises making more errors as much as them being reported more," said Bassett.
Consider:
- Details on 80 million US households exposed by unprotected cloud database
- 1.5 billion sensitive files exposed by misconfigured servers, storage and cloud services
- Saudi caller ID app leaves data of 5+ million users in unsecured MongoDB server
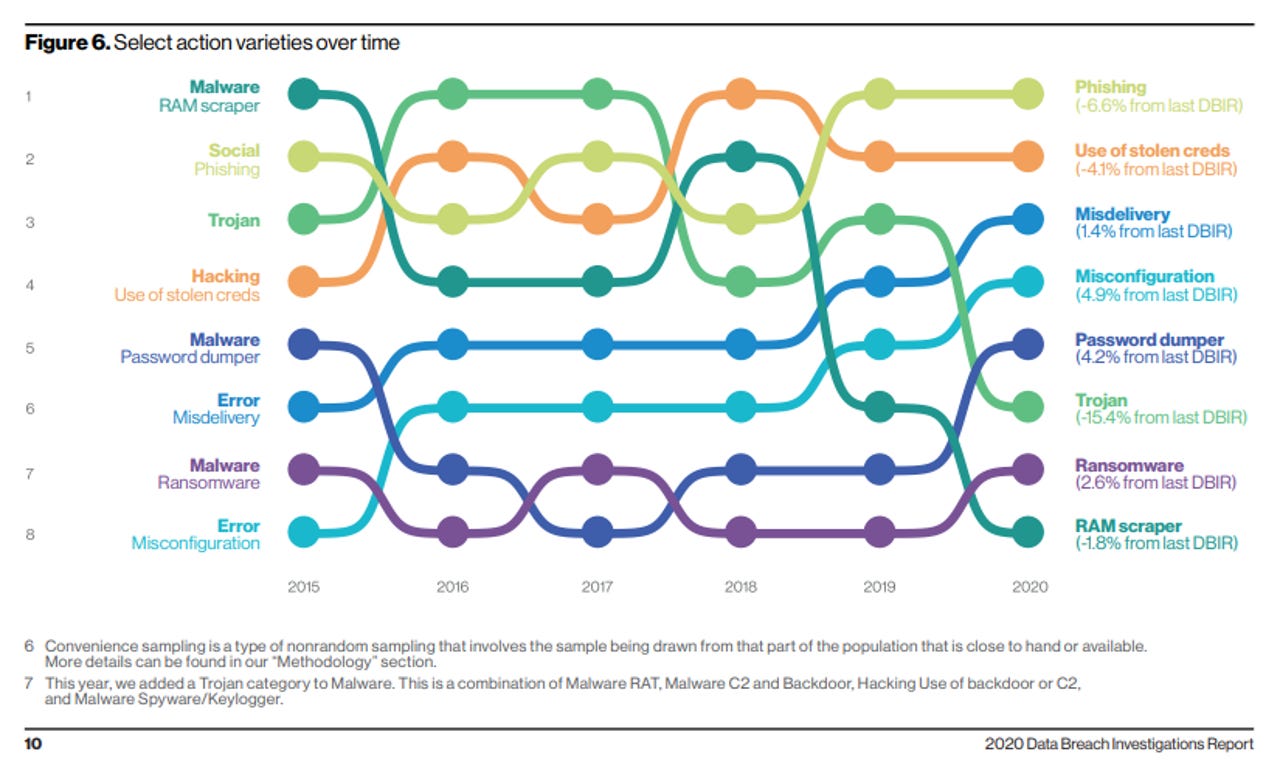
And that's just to name a few. This figure in Verizon's DBIR report tells the tale and shows how misconfiguration errors are trending.
Also: SMBs see cyberattacks that rhyme with large enterprises due to cloud shift
From the report:
Errors definitely win the award for best supporting action this year. They are now equally as common as Social breaches and more common than Malware, and are truly ubiquitous across all industries. Only Hacking remains higher, and that is due to credential theft and use, which we have already touched upon. Misconfiguration errors have been increasing. This can be, in large part, associated with internet-exposed storage discovered by security researchers and unrelated third parties.
Verizon's DBIR report is based on 81 contributing organizations in 81 countries. Verizon analyzed 157,525 incidents. Of those, 32,002 met quality standards and 3,950 were confirmed data breaches.
At a high level:
- 22% of breaches this year involved cloud assets and on-premises assets were in 71% of reported incidents.
- 45% of breaches featured hacking and 22% involved social attacks. 22% also involved malware.
- External actors were behind 70% of the breaches and organized crime in 55%. 30% involved internal actors.
- 81% of breaches were discovered in days or less.
- 72% involved large business victims.
- 58% of victims had personal data compromised.
- 86% of breaches were financially motivated.
- 43% of breaches involved web applications.
Other key takeaways from the Verizon DBIR include:
- Password dumper is the most popular form of malware followed by capture app data and ransomware.
- Office documents and Windows apps still tend to be the malware filetype of choice. Other filetypes seen as malware deliver mechanisms include shell scripts, Java, PDF, browsers app, Flash, Linux app, OSX app and Android app.
- 80% of breaches that include hacking are brute force or use of lost or stolen credentials.
- Phishing is the top form of social driven breaches. These social attacks arrived by email 96% of the time. Click rates on phishing remain at 3.4%.