Microsoft warns about Astaroth malware campaign

The Microsoft security team has issued a warning today about ongoing malware campaigns that are distributing the Astaroth malware using fileless and living-off-the-land techniques that make it harder for traditional antivirus solutions to spot the ongoing attacks.
The attacks were detected by the team behind Windows Defender ATP, the commercial version of the company's Windows Defender free antivirus.
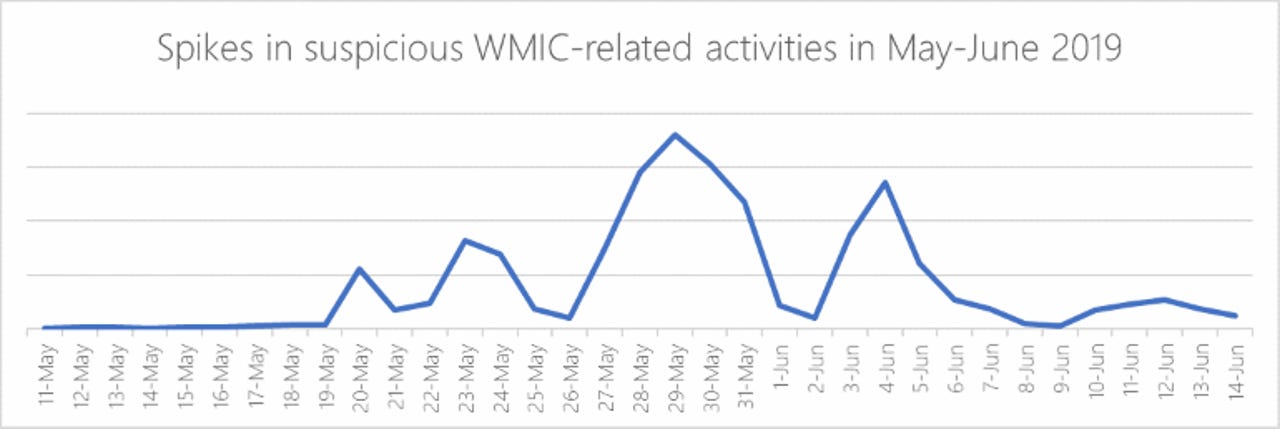
Andrea Lelli, a member of the Windows Defender ATP team said alarms bells sounded at Microsoft's offices when they detected a huge and sudden spike in usage of the Windows Management Instrumentation Command-line (WMIC) tool.
This is a legitimate tool that ships with all modern versions of Windows, but the sudden spike in usage suggested a pattern specific to malware campaigns.
When Microsoft looked closer, it discovered a malware campaign that consisted of a massive spam operation that was sending out emails with a link to a website hosting a .LNK shortcut file.
If users were careless to download and run this file, it would launch the WMIC tool, and then a plethora of other legitimate Windows tools, one after the other.
The tools would all download additional code and pass their output to one another, executing solely in memory -- in what's called fileless execution -- and without saving any files on disk, making the job of classic antivirus solutions harder, as they would have nothing to file on disk to scan.
In the end, the attack downloaded and ran the Astaroth trojan, a known info-stealer that can dump credentials for a wide category of apps, and uploaded the stolen data to a remote server.
The trojan, which was first seen in 2018, was also seen in a campaign targeting European and Brazilian users in February, this year.
The February campaign, detailed in great depth by Cybereason, was nearly identical to the one discovered by Microsoft active in May and June.
Just like the campaign spotted by Cybereason, the one detected by Microsoft also targeted Brazilian users. In en email, a Microsoft spokesperson told ZDNet that more than 95% of Astaroth infections were from Brazil.
Furthermore, almost the same tools and same infection chain were used, with the Astaroth operators going for the same fileless execution and living-off-the-land methods.
"It's interesting to note that at no point during the attack chain is any file run that's not a system tool," Lelli said in Microsoft's report on the May-June attacks, which the company published earlier today.
"This technique is called living off the land: using legitimate tools that are already present on the target system to masquerade as regular activity," Lelli said.
The technique has become incredibly popular with malware authors in the last three years and is now widely deployed.
The next step in the evolution of modern antivirus products is shifting from a classic file signature detection mode of operation to a behavioral-driven approach, where they can also detect "invisible" actions like fileless (in-memory) execution and living-off-the-land techniques where legitimate tools are abused for bad operations.
The Mac malware most likely to attack your PC this year
Related malware and cybercrime coverage:
- US Cyber Command issues alert about hackers exploiting Outlook vulnerability
- 'Silence' hackers hit banks in Bangladesh, India, Sri Lanka, and Kyrgyzstan
- Sodinokibi ransomware is now using a former Windows zero-day
- Hacker who launched DDoS attacks on Sony, EA, and Steam gets 27 months in prison
- UK's largest police forensics lab paid ransom demand to recover locked data
- Croatian government targeted by mysterious hackers
- More than 3B fake emails sent daily as phishing attacks persist TechRepublic
- Game of Thrones has the most malware of any pirated TV show CNET