Astaroth malware hides command servers in YouTube channel descriptions

Over the past year, the Astaroth infostealer trojan has evolved into one of today's stealthiest malware strains, containing a slew of anti-analysis and anti-sandbox checks to prevent security researchers from detecting and analyzing its operations.
Luckily, all these innovations are only used to target and infect users in one country alone -- namely Brazil.
The malware has historically targeted Brazilian users ever since it was first spotted in the wild in September 2018.
Cofense researchers were the first ones to detect and analyze the malware, followed by IBM researchers, then Cybereason, and then Microsoft, which analyzed its evolution across two separate blog posts, in July 2019 and March 2020.
Across all these reports, researchers noted how Astaroth slowly gained new features, developed a more complex infection chain, and shifted focus on stealth more than anything else.
A large collection of anti-analysis and anti-sandbox checks
In a new report published yesterday, Cisco Talos says that Astaroth has continued to evolve. The trojan still relies on email campaigns for distribution, fileless execution, and living off the land (LOLbins), but it has also gained two new major updates.
The first of these is a new and quite large collection of anti-analysis and anti-sandbox checks. The malware runs these checks before it executes to make sure it runs on a real computer, and not inside a sandbox environment, where it could be analyzed by security researchers.
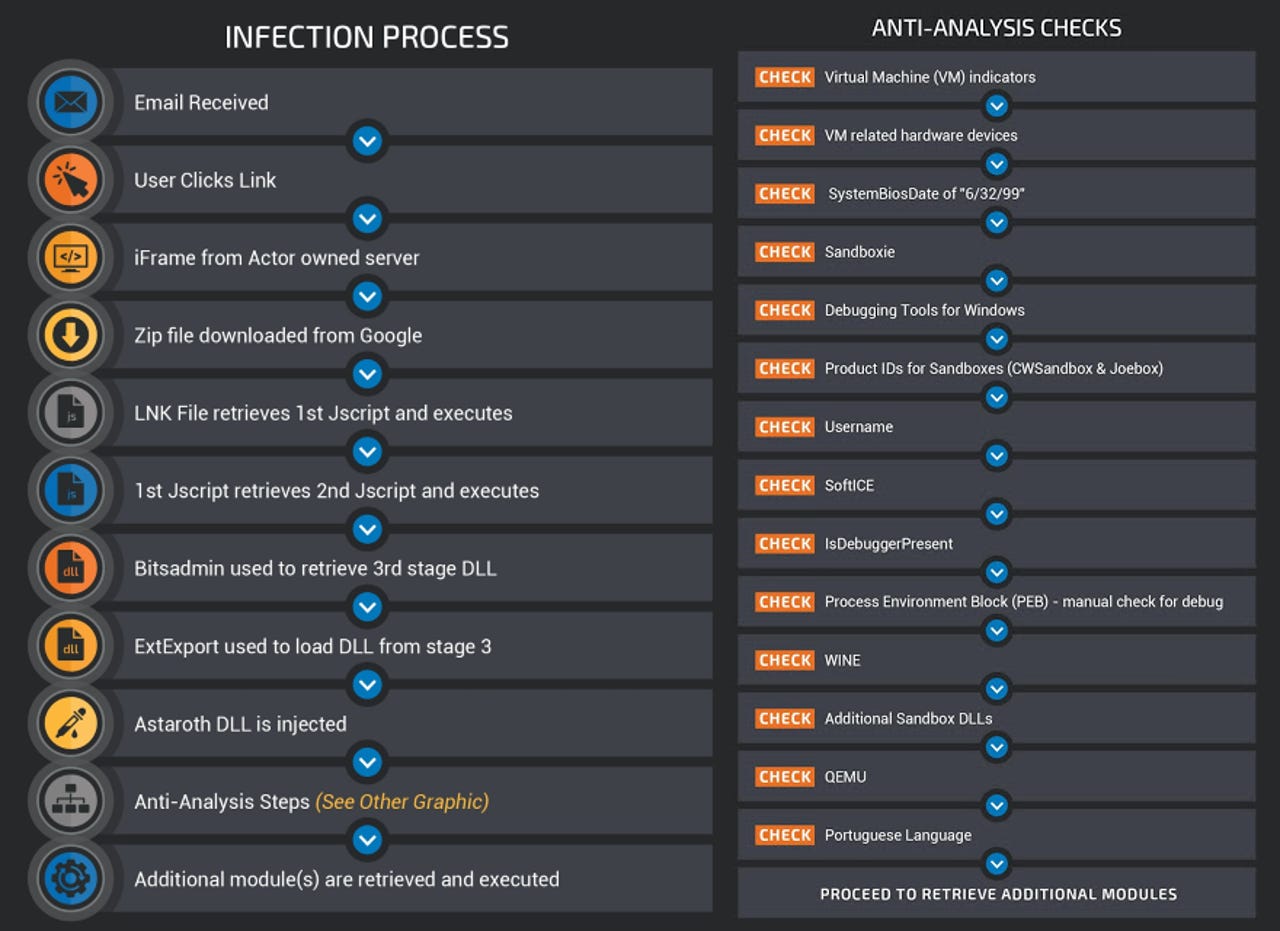
By avoiding having its operations analyzed, the Astaroth gang can avoid having payloads marked as malware. The longer the group stays under the radar of security solutions, the higher the infection rate, and the more data they can collect from victims and then sell online to other criminal groups for a profit.
"Astaroth is evasive by nature and its authors have taken every step to ensure its success," the Cisco Talos team said.
"They have implemented a complex maze of anti-analysis and anti-sandbox checks to prevent the malware from being detected or analyzed. Starting with effective and impactful lures, to layer after layer of obfuscation, all before any malicious intent was ever exposed. Then it finally proceeds through a rigorous gauntlet of checks for the tools and techniques of both researchers and sandbox technologies alike.
"This malware is, by design, painful to analyze," researchers added.
Hides C&C servers on YouTube
And if the malware wasn't hard enough to analyze, stopping its communications is also a tricky task. Following its most recent update, Astaroth now uses YouTube channel descriptions to hide the URL for its command and control (C2) servers.
According to Talos, after Astaroth infects a victim, the trojan connects to a YouTube channel, from where it retrieves the channel description field.
The field contains encrypted and base64-encoded text with the URLs of its command and control server. After decoding the text, Astaroth connects to these URLs to receive new instructions and to send stolen information for future storage.
One of the YouTube channels hiding the Astaroth C&C servers
This method of hiding the location of the C&C server on YouTube is not new. It's been used before in 2015 by Janicab and in 2019 by Stantinko.
However, in Astaroth, this method of hiding the C&C server URL on YouTube is only one of the three redundant methods of discovering and connecting to the C&C servers, Talos said, showing once again Astaroth's higher degree of sophistication when compared to other malware campaigns.
This means that even if YouTube takes down the channels, Astaroth shifts to another system to obtain its C&C servers.
For now, this trojan is only active in Brazil. If it ever gets unleashed onto the entire world, the trojan could cause a serious number of infections due to its complexity but also due to its rapid rate at which the trojan evolves.
Talos noted that in the past, Astaroth has always tried to stay one step ahead of security firms as much as possible by shifting to new infrastructure at regular intervals.